How to monitor network traffic via gateway mode(without http proxy)
Yesterday I was trying to reverse engineer one of my machine in order to analyze and extract APIs. I failed due to encryption method though, I learnt a new method to monitor network traffic. I did not know how to set http proxy on this machine at first, so I needed to find a way to monitor traffic as gateway mode. The solution is use mitmproxy as transparent proxying.
How to do it
Environment:
1 | Macbook with Ethernet port |
Connect your mac with Ethernet cable and share Internet via WIFI to the machine you want to monitor.
How to share Internet on MacOS: Go to Settings => General => Sharing => Internet Sharing
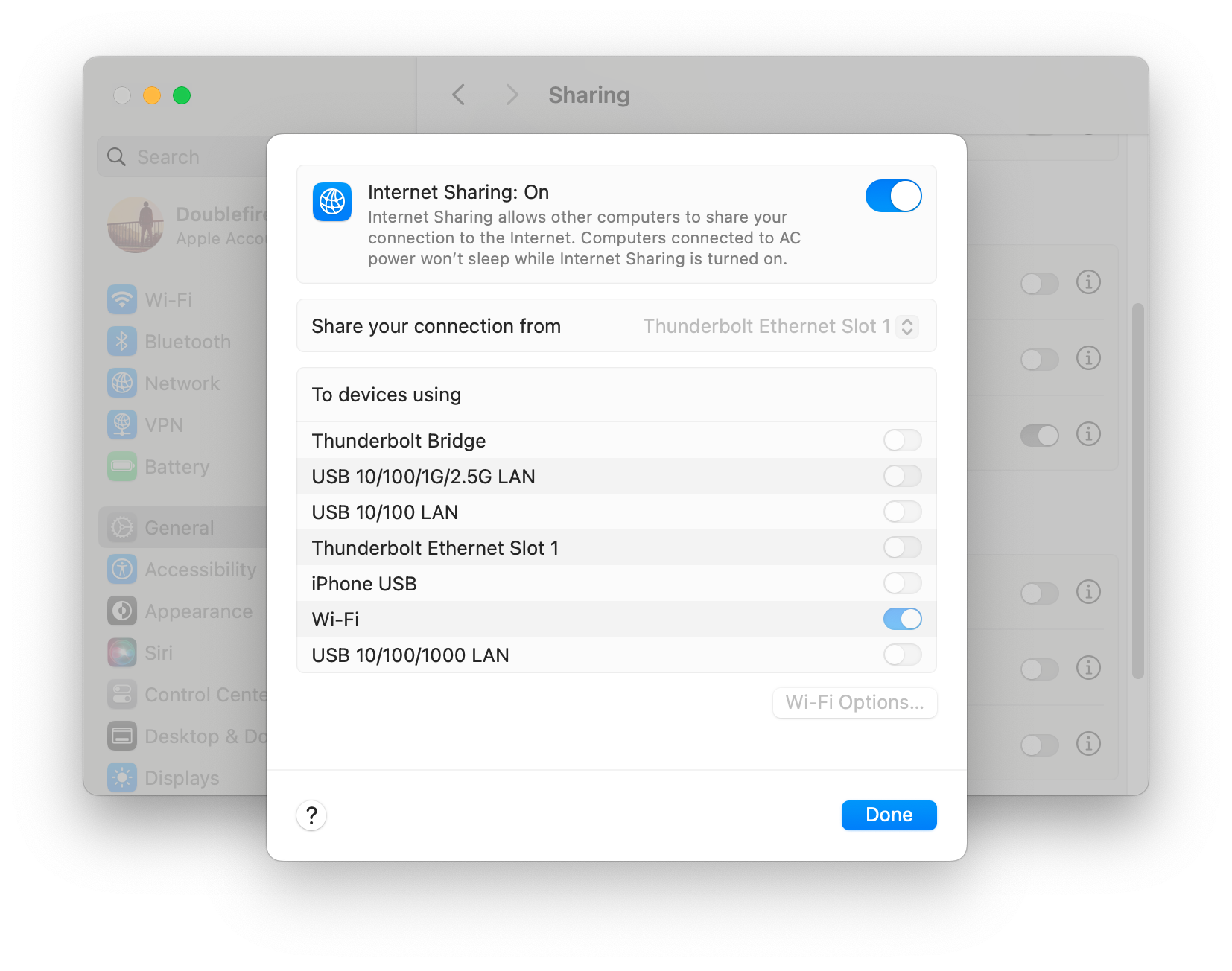
Open your terminal
1
2
3brew install mitmproxy
sudo sysctl -w net.inet.ip.forwarding=1 # Enable IP forwarding.
vim pf.conf # Edit config file1
rdr pass on bridge100 inet proto tcp to any port {80, 443} -> 127.0.0.1 port 8080
This rule tells pf to redirect all traffic destined for port 80 or 443 to the local mitmproxy instance running on port 8080. You should replace
bridge100with the interface on which your test device will appear. I think your ethernet interface should be the same as me because you share internet same way as me. You can double check viaifconfig.1
2
3sudo pfctl -f pf.conf # Configure pf with the rules
sudo pfctl -e # Enable configuration
sudo vim /etc/sudoers # add content below in the end of /etc/sudoers1
ALL ALL=NOPASSWD: /sbin/pfctl -s state
Note that this allows any user on the system to run the command
/sbin/pfctl -s stateas root without a password. This only allows inspection of the state table, so should not be an undue security risk. If you’re special feel free to tighten the restriction up to the user running mitmproxy.1
mitmproxy --mode transparent --showhost # view traffic in terminal
or
1
mitmweb --mode transparent --showhost # view traffic in webpage http://127.0.0.1:8081/
Make your device which you want to monitor traffic connect to the wifi shared by Macbook.
Then open mitm.it in browser on the device to install certificate in order to catch https package. Then happy reverse engineering!